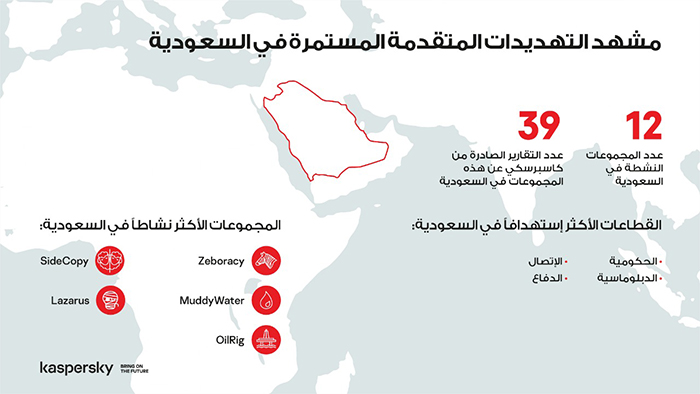
Kaspersky researchers have kept a close eye on Saudi Arabia for Advanced Persistent Threats (APT) and have worked on 39 investigative reports related to 12 cyber gangs actively targeting the country since the start of the pandemic in 2020.
Kaspersky researchers issued 39 threat intelligence reports on investigations associated with APT groups targeting Saudi Arabia. The country has the second-highest number of reports coming out of all the Middle Eastern countries, making it one of the most targeted countries in the region. Kaspersky has found that these APT groups primarily target Saudi governmental and diplomatic institutions as well as educational and telecommunication organizations. Other targeted entities include financial institutions, IT companies, healthcare, law firms, military and defence. Some of the notorious APT groups investigated in Saudi Arabia are the Lazarus, MuddyWater, Oil Rig and SideCopy.
The research team has found that Exploit Public facing Applications, Valid Accounts, and Phishing are the most commons attack vectors against Saudi Arabian infrastructures. For example, MuddyWater, a Middle Eastern espionage motivated APT group that targets government, telco and oil companies to derive information, using compromised accounts to send spearphishing emails with targeted attachments to recipients. Zeboracy is a trojan that is deployed as part of cyber espionage campaigns to collect initial data from compromised systems. OilRig is another Middle Eastern APT targeting organizations that have presence across multiple industries using social engineering techniques. The SideCopy APT group carries out malware campaigns targeting entities for espionage purposes. The Lazarus APT group uses the watering hole attack strategy in which they observe which websites are frequented by an organization and infects one or more of them with malware.
Abdessabour Arous, Security Researcher, GReAT, Kaspersky commented: “Targeted threats are getting more and more sophisticated every day. Investigating and reporting on these groups provides us great visibility into their motives and movements. From each report, we are able to form deeper insights, and equip relevant stakeholders with knowledge they need to remain protected. Today, all organisations have a pressing need to stay informed; as this allows security teams to predict what the attacker’s next move would be and take appropriate steps to protect themselves against future incidents.”
Nouf Alqahtani, Cyber Threat Intelligence Senior Analyst at STC, said: ““Company employees are known to be the first line of defense against cyberattacks and shoulder the responsibility to protect data, which is the most important asset of any organization. To strengthen this line and make it impenetrable, it is imperative that organizations give cybersecurity trainings and education an equal footing across the board within the company. Perhaps make each employee across the hierarchy compliant to learn about secure ways of operating devices, sharing data internally and externally and understand the evolving nature of cybercrime. Employees knowledgeable in cybersecurity know what red flags look like when company networks, devices and information are under threat. After employees, I believe defense is started by threat intelligence, and organizations should be driven by Threat intelligence”
Artificial Intelligence, the Internet of Things, Blockchain, Fintech, and 5G are rapidly gaining traction across Saudi Arabia’s public and private sectors. The country is poised to become a global leader in the digital economy, and increasing connectivity often correlates with an increase in targeted cyber threats. The country has geared itself up to tackle even the most challenging cybersecurity attacks by placing cybersecurity at the forefront of its digital transformation. According to the Global Cybersecurity Index, Saudi Arabia ranked firstin the MENA region in its commitment towards cybersecurity. Further reaffirming the government’s dedication towards improving its cybersecurity capabilities.
Kaspersky continuously monitors APT groups and provides unique ongoing access to investigations and discoveries, including full technical data, provided in a range of formats, on each APT as it emerges. Kaspersky works with legal authorities and shares intelligence needed to track and prosecute the groups behind such attacks.

COMMENTS